
Read application properties from Azure
How to read secret application properties from Azure Key Vault.
Introduction 0.
We all met a task where you have to define how to manage sensitive properties in the deployment environment. Sometimes the pre-existing clients’ environment sets their own requirements for this task.
It was our case. We had to integrate with existing Azure-based infrastructure. Sensitive data were already stored in Azure KeyValue .
From the other side, we already had a Spring Boot application. The application should take specific secrets (such a DB password) from the existing storage to use them in application properties.
Here we go.
Please, check out the repo if you’re lazy to read: GitHub link.

What is Azure Key Value 1.
Just to refresh your memory. Azure is a Cloud Service developed by Microsoft.
It provides a broad set of services for building, deploying, monitoring, etc.
Key Vault is a part of the family of this services.
KeyVault is used to store and get secrets securely.
These could be secret properties (the article case), passwords, keys, or certificates.

Set up Azure Key Value 2.
The first step is setting up Azure Key Vault.
You have to create an Azure account for this.
You get access to Azure Portal as soon as you successfully sign up.
We have to create an Azure Key Vault instance where we place our secrets.
Then we add the secret property itself. We should do it in the Secrets tab.
Let’s call our property shardik--db-password as soon as it’s most used secret property in a typical Spring Boot application.
Note: we have to provide a specific kind of application listener to read the property before any tool which uses DB connections.
It could be Spring itself, Hibernate, Hikari, etc.
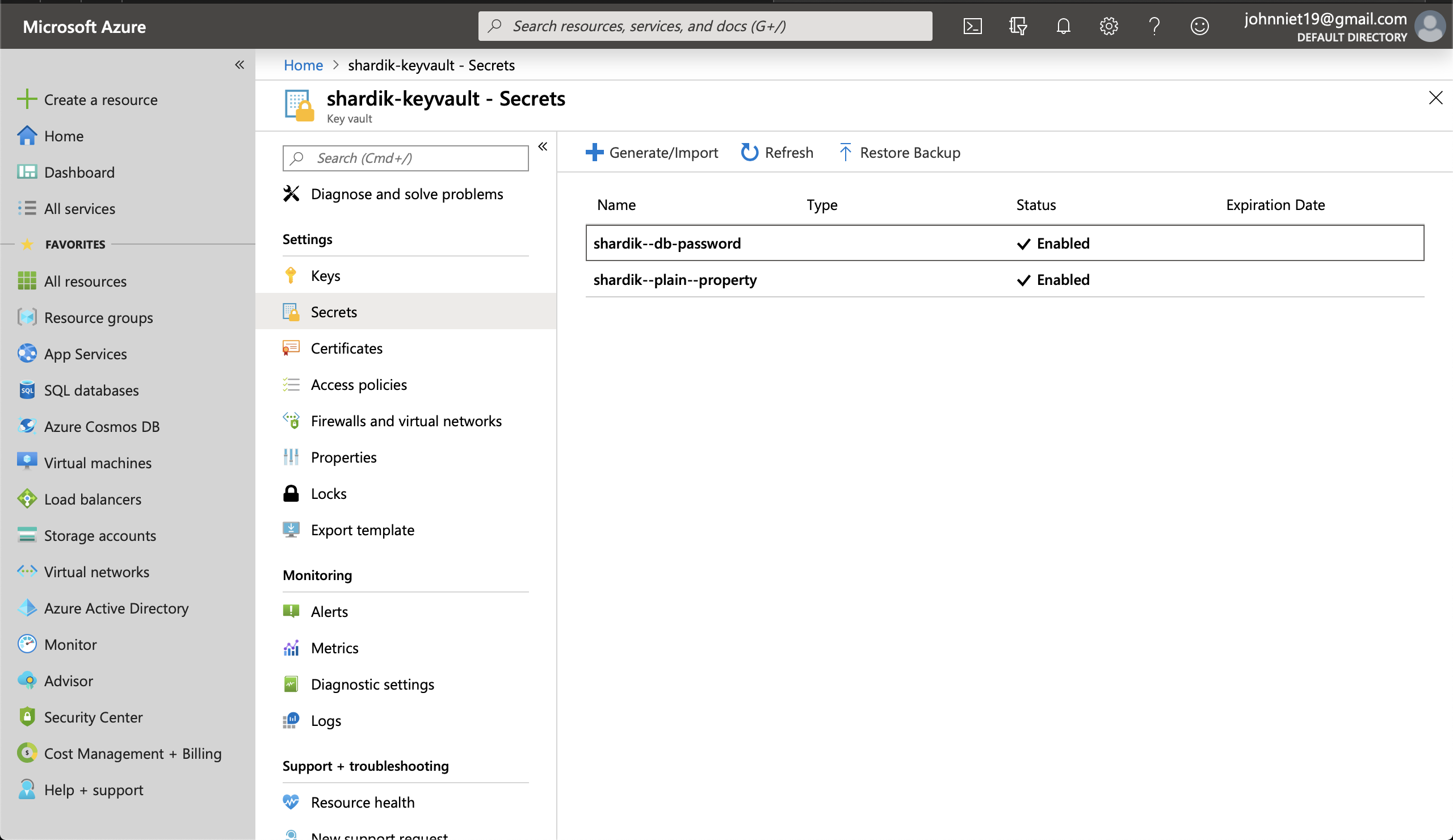 We have to extract a few access properties to connect our Spring application.
We have to extract a few access properties to connect our Spring application.
AZURE_KEY_VAULT_APPLICATION_ID=application_id_value
AZURE_KEY_VAULT_CLIENT_SECRET=client_secret_value
AZURE_KEY_VAULT_BASE_URL=azure_base_url_value
Later we will use them to configure an Azure client within the app.
Dependencies
We used the following Azure Java SDKs:
Azure Client 3.
Now we have to create Azure client:
KeyVaultClientCredentials is a custom implementation for azure KeyVaultCredentials
It requires two properties from the Azure portal, which we read previously. We save them as environment variables in the sample app case.
We’re ready to use this client in the app listener to read secrets.
Application Listener 4.
As I mentioned, the sample case reads the database password from the Azure Key Vault.
This requires to use an application listener to catch up Application Context event on the application starting.
As soon as the application starting event is caught, we have to read secret properties
from Azure (readApplicationPropertiesFromAzure()) and set them to Spring Boot application properties.
They will be read by other consumers from the expected place then.
Note: do not forget to add src/main/resources/META-INF/spring.factories with following content:
Spring factories’ configuration is required to register an application listener.
Reading the properties 5.
Here we read secrets from Azure Key Vault with getSecrets(baseUrl) method.
Note: key vault doesn’t support dots in a secret name. The pretty simple hack works well here.
We replaced dots with dashes within Key Vault.
And we do replace in reverse before adding secret as a Spring Boot variables.
Conclusion
There are plenty of ways to store and read sensitive properties in the Spring Boot application.
Azure Key Vault is one of them if your infrastructure requires this.
You can also manage certificates in the Keystore based on Azure Key Vault.
It’s a more complicated case. But it’s solved by Shardik too.
The article is coming soon.
Be free to ask us any questions. Code with Shardik.
